Third party security review policy

Third-Party Security: 8 Steps To Assessing Risks And Protecting Your Ecosystem
Senior Content Marketing Manager at Secureframe
Senior Compliance Manager at Secureframe
The average company shares confidential information with 583 third-party vendors — and 82% of companies provide those third parties with access to their sensitive data.
In today’s interconnected business landscape, an organization’s attack surface extends far beyond its own IT infrastructure. Assessing and managing third-party risks is essential for protecting your operations against external threats.
Below, we’ll dig into the importance of third-party security, share a step-by-step process for assessing third-party risk, and define KPIs for measuring the success of your TPRM program.
Understanding third-party risk management (TPRM): What is third-party security?
Third-party vendors are companies that have access to your organization’s sensitive data assets, such as service providers, cloud computing platforms, data centers, payroll processors, and suppliers.
While working with third-party vendors allows organizations to scale faster, improve processes, and work more efficiently, they also introduce risk. Every third-party vendor that has access to your systems offers malicious actors a potential point of access to your sensitive company or customer data.
According to a Verizon Data Breach Investigations Report, 62% of all data breaches happen via third-party vendors.
This is why third-party security is so essential — having a set of practices and tools that can help identify third-party risks and reduce their likelihood and impact can protect your organization and your customers from serious threats. Not to mention, failure to properly manage third-party risks can expose your organization to regulatory, financial, legal, and reputational damages.

TPRM Resources Kit
The threat of third-party security risk in 2024
Third-party risks continue to evolve alongside the larger information security landscape. New technologies such as AI, shifting global business practices, new legislation and regulatory requirements, and other factors make strong third-party risk management practices critical for organizations in 2024 and beyond.
- In the past two years, 82% of organizations have experienced one or more data breaches caused by a third party, costing an average of $7.5 million to remediate.
- Only 34% of respondents have confidence that a primary third party would notify them of a security incident or data breach.
- 98% of organizations have vendor relationships with at least one third party that has experienced a breach in the last two years.
- For every third-party vendor in their supply chain, organizations typically have indirect relationships with 60 to 90 times that number of fourth-party relationships.
- Compared to the primary organization, third-party vendors are five times more likely to exhibit poor security. Approximately 10% of third-party vendors receive an F rating among organizations that earn an A rating for their own security posture.
- On average, the identification and containment of a supply chain breach takes 26 days longer than the global average for other types of breaches.
Recommended reading

Vendor Risk Management (VRM): How to Implement a VRM Program that Prevents Third-Party Breaches
Types of third-party security risk
Partnering with third-party vendors can introduce several types of risk to your organization. Below are many of the most common risks to be aware of as you build out a third-party risk management program.

- Cybersecurity risk: The risk of a data security breach or cyber attack on a third party that has access to your organization’s systems or data assets, allowing hackers or other malicious actors unauthorized access to your networks.
- Compliance risk: Many regulations require organizations to conduct due diligence to ensure any vendors they work with have adequate data protections in place. For example, HIPAA requires healthcare organizations to verify that their business associates safeguard PHI. If a third-party vendor does not adhere to regulatory and legal requirements, your organization can be exposed to violation penalties.
- Reputational risk: If a data breach, security incident, or poor business practices are brought to light at a third-party vendor, your organization could suffer reputational damage by association.
- Financial risk: If a third party you rely on faces financial difficulties or bankruptcy, your organization could suffer lost revenue or excess costs — especially if you rely heavily on their services or products.
- Operational risk: The risk of the third party failing to deliver services or products as expected, which can disrupt your business operations and customer commitments.
- Strategic risk: If a third-party vendor’s strategic goals don’t align with your organization’s, their strategies or operations may change in a way that is detrimental to your business.
How to conduct a third-party security risk assessment
A third-party risk assessment is an essential tool for understanding, quantifying, and reducing any risks associated with third-party vendors and suppliers. These risk assessments are important for a few key reasons:
- They offer a better understanding of the level and types of risk you would assume with each vendor relationship. Armed with this knowledge, you’ll be able to make more informed decisions about how to manage and mitigate those risks effectively — or avoid taking on unnecessary risk altogether.
- They give you critical insights into a vendor’s cybersecurity and data privacy practices. When you grant a vendor access to your IT environment, you need assurance that they take cybersecurity as seriously as you do. A risk assessment or due diligence questionnaire can help you understand the security controls they’ve put in place and how well-protected your sensitive data would be in the event of an external attack.
- You’ll be able to verify your own level of compliance with any regulations or industry standards that require you to work with compliant vendors, such as GDPR, CCPA, NYDFS, PCI DSS, and HIPAA. You’ll also satisfy compliance requirements for regulations that require regular third-party risk assessments.
- You’ll take a proactive approach to protecting your company’s financial and reputational health. Association with a compromised vendor could have major implications for your business, with both immediate financial consequences and loss of customer trust.
Here’s a step-by-step guide on how to complete a third-party risk assessment.
Step 1: Determine an acceptable level of third-party risk
Acceptable levels of third-party risk are often dictated by the organization’s strategic goals, regulatory environment, operating capabilities, and financial capacity.
Different business units may also have different risk tolerances, so decisions about acceptable levels of risk should involve multiple stakeholders across the organization. Include senior management, legal teams, IT, security, compliance, and operations personnel in discussions about defining an acceptable level of risk.
Step 2. Identify relevant risks
Different vendors also carry different levels of risk. Here are a few questions to help identify potential third-party risks:
- Would the vendor have access to internal networks? What level of access would be granted?
- Are there specific regulatory requirements associated with the supplier, such as HIPAA or GDPR?
- Does the vendor rely on other third parties that could pose a risk to their service delivery? How do they manage and monitor their own supply chain risks?
- Has the vendor had any history of breaches or incidents?
- Is the vendor SOC 2 or ISO 27001 compliant?
- What measures does the vendor have in place to ensure business continuity in the event of a disaster?
Step 3: Assess the third-party vendor’s current control environment and cybersecurity posture
Due diligence or a security questionnaire should always be part of your vendor procurement process. Make sure any vendors you might partner with meet your security requirements before moving forward.
- Which security controls do they currently have in place to mitigate risk?
- Which security standards are they compliant with, and when did they complete their most recent external audit?
- Has the supplier suffered a data breach or major security incident, or been subject to regulatory intervention?
- Does the vendor have an incident response plan in place? Does that plan include notifying your organization of a security incident or data breach?
- Does the vendor have a robust business continuity and disaster recovery plan? How have they managed past disruptions or crises?
- Do they perform regular penetration tests, vulnerability scans, or internal security audits?
If you’re not sure what to ask, check out our vendor security questionnaire template for a comprehensive list of security assessment questions.
Recommended reading

How to Use SIG Questionnaires for Better Third-Party Risk Management
Step 4: Understand any fourth-party risks
Will this vendor subcontract any operations to other vendors? Many organizations have limited visibility into or control over fourth-party relationships, yet these subcontractors can also introduce significant risks to your business operations.
To mitigate fourth-party risks effectively, organizations need to extend their risk management frameworks and due diligence processes beyond direct vendors to ensure third-party vendors manage their subcontractors effectively.
Ask vendors about their own third-party risk management programs to understand how they evaluate and monitor fourth-party vendors. It’s also recommended to include fourth-party risk clauses in vendor contracts:
- Include a clause that allows you to audit the third-party vendor’s management of subcontractors, or requires them to provide audit reports.
- Stipulate that third-party vendors must ensure their subcontractors comply with a specific security, privacy, and/or compliance standard relevant to your industry, such as SOC 2, ISO 27001, HIPAA, or NIST 800-53.
- Define liability in the event of a fourth-party security breach or data loss.
- Require that the third party notify you promptly of any issues with subcontractors that could affect your organization.
- Require third-party vendors to disclose information about key subcontractors that are involved in critical business operations or handle sensitive data.
- Consider requiring third-party vendors to have cybersecurity insurance that covers damages caused by subcontractors.
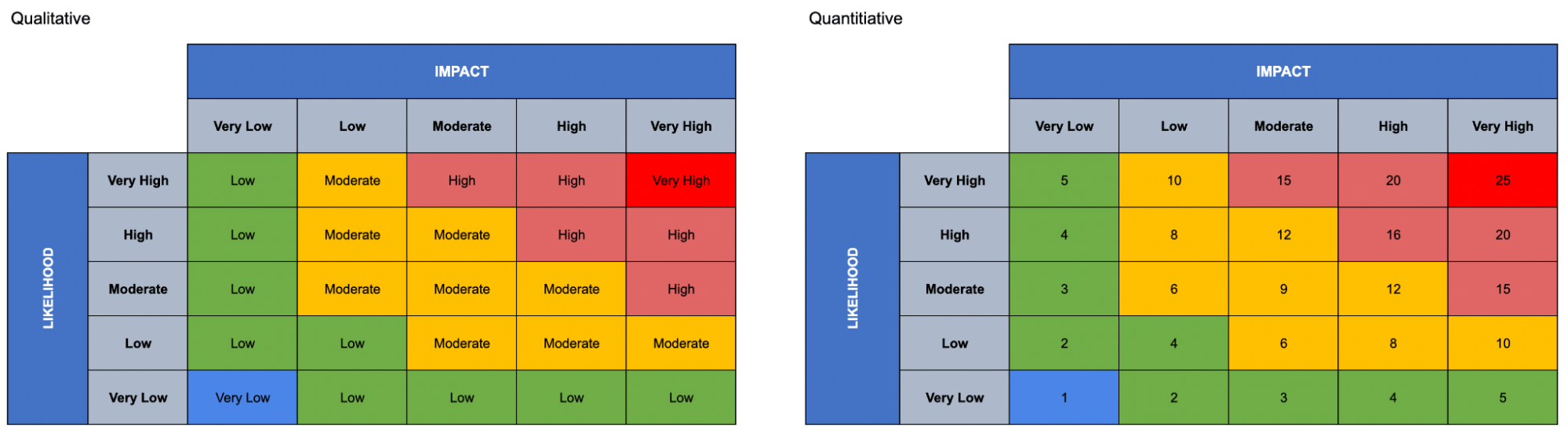
Step 5: Classify third-party risks using a risk register and risk matrix
Next, you’ll need to assess the potential likelihood and impact of each vendor risk. This will make it easier to prioritize risks, compare vendors, and focus on mitigating the most urgent risks posed to your organization.
Add third-party risks to your risk register to maintain a comprehensive view of your organization’s risk profile and attack surface. Then use a risk matrix to prioritize third-party risks and create a mitigation plan.
A risk matrix ranks risks based on likelihood and impact scores. Risks that are both highly likely to occur and would have a significant impact on your business are given higher priority than less severe risks.
The Secureframe platform uses both qualitative and quantitative scales for its risk register feature:
Step 6: Select a third-party vendor and establish mitigating controls
After creating a short list of third-party vendors to partner with, you may require them to implement additional controls to win your business.
Include any minimum service levels or core security and compliance requirements in your vendor contract — for example, that the vendor is required to maintain an active ISO 27001 certification or undergo an annual SOC 2 audit.
Step 7: Continuously monitor third-party risk
Third-party risk assessments aren’t a one-and-done deal. After onboarding a new vendor, continue conducting third-party risk assessments on an annual basis to maintain a clear and up-to-date picture of your risk environment. Update vendor risk scores as necessary, and flag any vendors that exceed your established risk threshold.
Step 8: Define a vendor exit strategy
If a new risk assessment reveals that a vendor no longer meets your acceptable level of risk, you may decide to terminate the relationship. Properly offboarding a vendor is just as important as successfully onboarding one, so have a plan for every step in the vendor lifecycle.
During offboarding, you’ll need to remove a vendor’s access to your IT infrastructure and data assets to maintain strong security and reduce the risk of a breach. Make sure you:
- Deauthorize all vendor accounts and login credentials, including shared credentials
- Deauthorize credentials to APIs, VPNs, file sharing, and messaging apps
- Request any company equipment be returned
- Revoke any physical access granted to data centers or information assets
- Ensure any data obtained by the vendor has been properly disposed of
- Maintain access logs for audit trails and to detect unauthorized access attempts
Metrics & KPIs to measure third-party risk management program success
Measuring the effectiveness of your third-party risk management program involves several key metrics. These KPIs and KRIs can help assess how well you’re managing the risks associated with third-party relationships.
These metrics include:
- Number of vendors without a current risk assessment: Establishing a vendor risk management policy can ensure that everyone in your organization adheres to requirements and follows the defined third-party risk assessment process.
- Pass rate for security questionnaires: If every vendor you evaluate satisfies your security requirements, they likely aren’t stringent enough. Ensure questionnaires offer a comprehensive assessment of the vendor’s risk management practices and security controls.
- Number of current compliance issues or security findings: The greater the number of issues, the more likely the vendor is to experience regulatory compliance penalties or violations. Non-compliant vendors have major implications for your own compliance status.
- Compliance rate: Percentage of third parties compliant with your organization’s security policies and standards.
- Incident response time: Time taken to identify and respond to security incidents involving third parties.
- Risk mitigation effectiveness: Evaluate how effectively identified third-party risks are mitigated or managed. This can include reviewing the success of implemented controls.
- Fourth-party risk exposure: Understand the risk posed by your third parties' own vendors. It's critical to know how well your third parties manage downstream risks.
Strengthen your third-party security risk management with Secureframe
Secureframe’s GRC automation platform features robust vendor management and an end-to-end risk management solution to help you build and maintain a strong security posture.
- AI-enhanced risk assessment workflows identify risk, assign risk scores, and suggest risk treatment plans in just a few clicks.
- Document risk treatment plans and view risk history to show auditors and stakeholders the steps you’ve taken to mitigate risk and strengthen your security posture.
- Build out your risk register with our comprehensive risk library that includes NIST risk scenarios for categories like Fraud, Legal, Finance, and IT.
- Track control health and flag vulnerabilities with continuous monitoring across your tech stack.
- Use automation, machine learning, and Secureframe’s Knowledge Base to automate responses to security questionnaires and RFPs.
- Use a Secureframe Trust Center to demonstrate to third parties your own compliance and security posture
Learn more about how Secureframe can streamline security and compliance and improve your risk management by scheduling a demo with a product expert.
Use trust to accelerate growth
Third-party security FAQs
What is 3rd party security?
Third-party security refers to the practices and measures that an organization uses to ensure that its third-party vendors, partners, or service providers maintain adequate security to protect sensitive data and IT systems. Since these third parties often have access to or handle critical business data, managing their security risks is crucial. Third-party security involves assessing and managing the risks posed by external entities to an organization's data and IT infrastructure.
What is third-party access security?
Third-party access security is a more specific aspect of third-party security, focusing on controlling and securing the access granted to third parties. It includes managing credentials, defining access privileges, and monitoring and auditing third-party activities within an organization's network. The goal is to ensure that third parties have only the necessary level of access to perform their roles, thereby reducing the risk of data breaches or unauthorized activities.
What is a third-party security provider?
A third-party security provider is an external company or service that offers cybersecurity services to other organizations. These services can include security assessments, monitoring, cybersecurity solutions, and incident response. Companies often enlist third-party security providers to enhance their security capabilities, benefit from specialized expertise, and address specific security needs that they may not be able to manage internally.
What is the difference between first-party security and third-party security?
While first-party security is focused on an organization's internal cybersecurity efforts, third-party security extends these efforts to the external parties the organization interacts with.
- First-Party Security: This pertains to the security measures an organization implements for its own systems and data. It involves protecting the organization's internal IT infrastructure, data, applications, and networks from cyber threats. First-party security is fully under the control of the organization.
- Third-Party Security: In contrast, third-party security involves ensuring that external entities (like vendors, partners, or service providers) that have access to or manage an organization's data and systems also maintain adequate security standards. Third-party security is more about managing external risks and requires collaboration and coordination with entities outside the organization.







